About Policy Inheritance
Table of Contents
A policy is a collection of checks and monitors you create and apply to assets. Policies reflect your Standard Operating Procedures (SOPs). For example, you can use a policy to configure Windows updates, monitor the event log, and schedule scripts.
Once you create your policies, you can assign them to assets both directly and indirectly through folders.
This is called policy inheritance, or “cascading policies," which works similarly to GPO. Policy inheritance can help you build complex structures as your business grows.
You can read on, or watch this short video to learn more:
View the Effective Policy
To see the Effective Policy (i.e., the sum of all policies currently being merged and applied to a folder or asset), navigate to the (Customer) Organizations tab, then select a specific Organization.
Click the Assets & Policies subtab, then click Show Effective Policy:
Syncro displays the Policy Overview tab of the Policy Builder, a read-only view of everything currently enabled or disabled on the policy at any given level:

An Example of Policy Inheritance
On a Customer's Assets & Policies subtab, you'll notice a folder/file structure not unlike you'd have in Windows for managing sites or further segregating assets.
Folders can contain sub-folders (up to five sub-folders deep) and assets, which can live at any folder level.
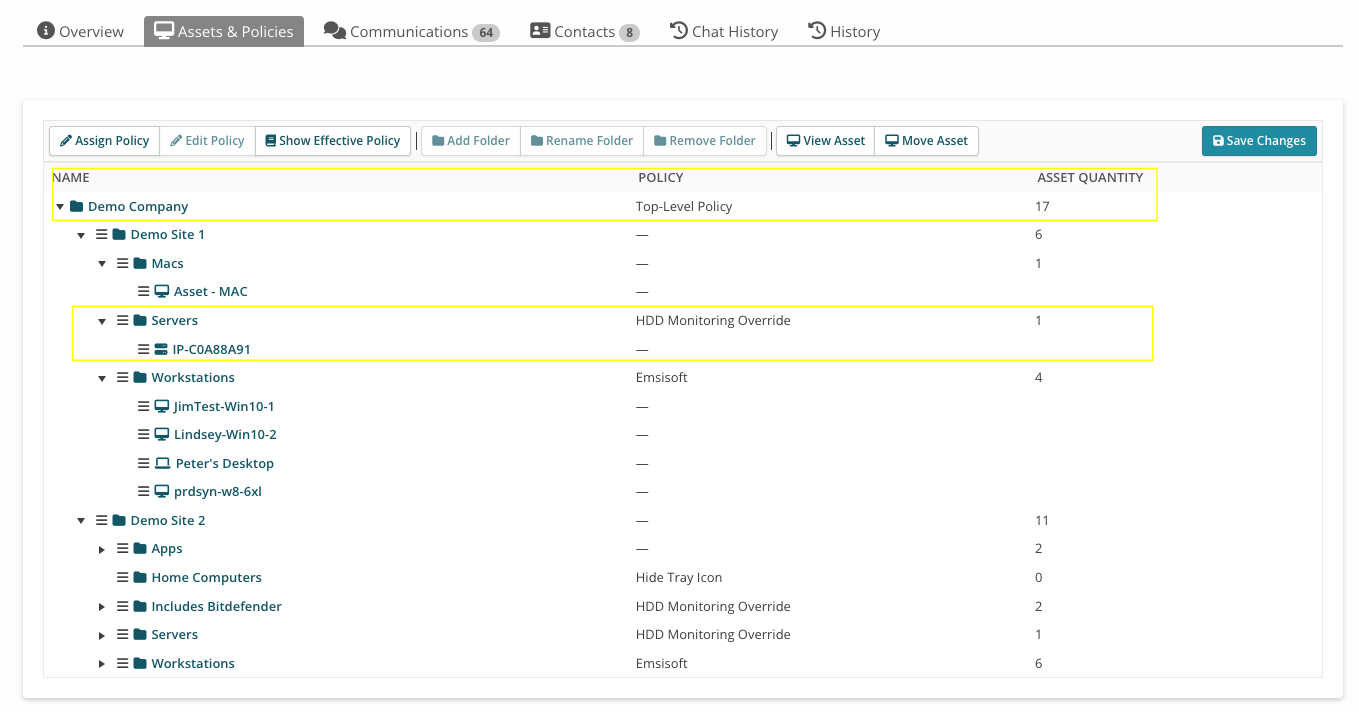
Top-level folders corresponding to your Customer accounts are labeled with your Customer names, and considered the parent folder. In this example:
- Demo Company is the Customer (top-level) folder shown.
- Demo Site 1 and Demo Site 2 are sub-folders.
- Inside the Demo Site 1 sub-folder are three sub-folders: Macs, Servers, and Workstations, and inside each of these sub-folders are assets (e.g. for Servers, the asset is called IP-COA88A91).
- Inside Demo Site 2 are five subfolders.
Look at the POLICY column to see what policy is being applied at each level:
- The three sub-folders of Demo Site 1 and the 5 sub-folders of Demo Site 2 inherit the policy called Top-Level Policy, because they're assigned to the Customer (top-level folder) named Demo Company and don't have any policies specifically applied to them (noted by the “—” in the POLICY column).
- The IP-COA88A91 asset inherits the policy called HDD Monitoring Override from the Servers sub-folder, as well as Top-Level Policy from the Demo Company folder.
- The assets in the Workstations folder inherit the Emsisoft policy and Top-Level Policy. See also: Emsisoft.
Rules of Policy Inheritance
The basic rules are:
- Top-level folders that correspond to your Customer accounts can't be deleted nor renamed.
- You can have an unlimited number of folders at each level, up to five levels deep (not counting the top-level Customer folder).
- You can assign one policy to each folder or asset.
The important rules of policy inheritance are as follows:
- All policy assignment is done at the Customer level.
- Exception: You can bulk assign one policy to ALL top-level folders within each customer, or those who do not currently have a policy in their top-level Customer folder:

- Exception: You can bulk assign one policy to ALL top-level folders within each customer, or those who do not currently have a policy in their top-level Customer folder:
- When you assign a policy to a folder, that policy propagates down to ALL the sub-folders and any assets within them.
- Policies at any level inherit all the policies above them.
- If any sub-folder or asset has its own policy assigned, that folder/asset-specific policy is combined with any parents' policies. This is called the Effective Policy.
- Policy settings from a child level that conflict with a parent level will override the parent level.
- Exceptions: Drive monitors, scripts, system tray items, third-party patches and Windows updates—are additive. For example, if the current policy has script B, and its parent policy has script A, then the effective policy will run both scripts A and B.
- While assets do not explicitly need a policy assigned (given they inherit their effective policy based on their placement in the inheritance tree), you may find it useful to add asset-specific settings and overrides for exceptions by applying a policy directly to an asset.
